Resolving Vulnerability Remediation Challenges
In the first post of this series, l will be covering two common challenges that are usually encountered by vulnerability managment teams. These challenges include how to efficiently prioritize findings from thousands of vulnerabilities and correlate/track vulnerabilities from different sources [i.e penetration test reports or security testing tools like Nessus, Acunetix, Burpsuite etc.].
CHALLENGE 1: Prioritizing Findings from Thousands of Vulnerabilities
In my experience, the below prioritization process has been very effective in ensuring that true high-risk vulnerabilities are remediated first.
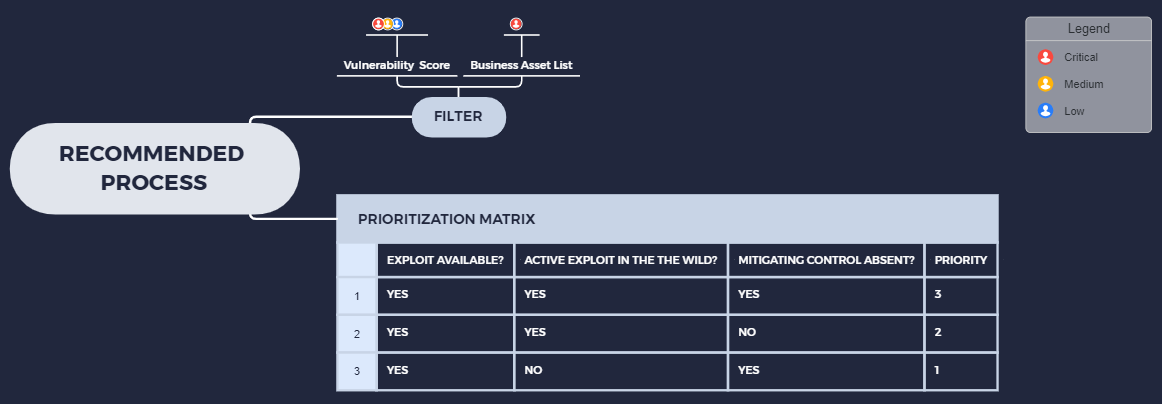
As shown above, the first thing after identifying high CVE/CVSS scores on a critical business asset list is to filter for three (3) checks with increasing order of priority and then work with the smallest sample size first. Check:
- If exploit code has been written or published for it
- If the vulnerability has been exploited in recent real-world attacks
- Finally, look at the attack profile to identify if controls are currently in place to mitigate the vulnerability.
For example, the below filter was able to narrow down 64 vulnerabilities to 1 vulnerability. This process provides a practical way of prioritizing remediation of the most serious vulnerabilities first.
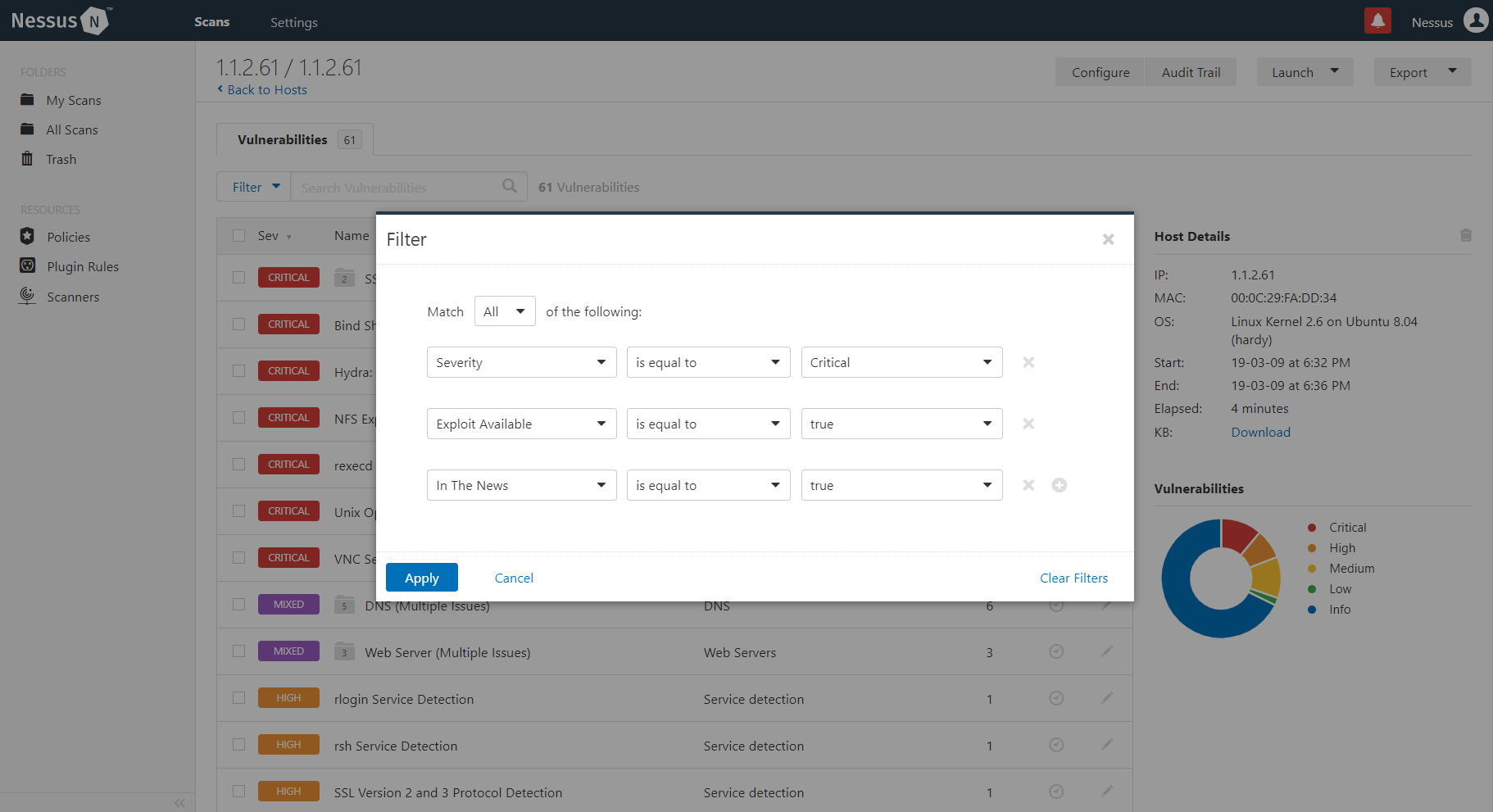
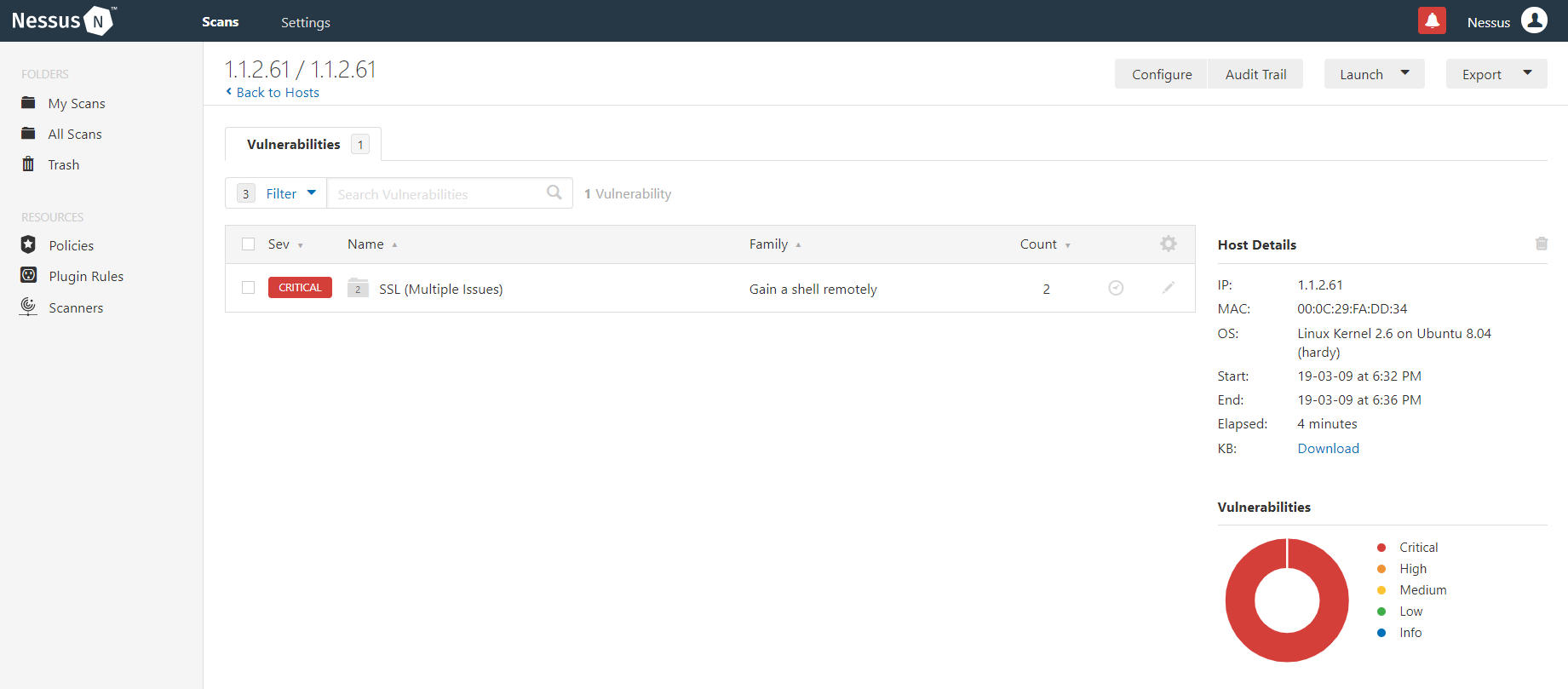
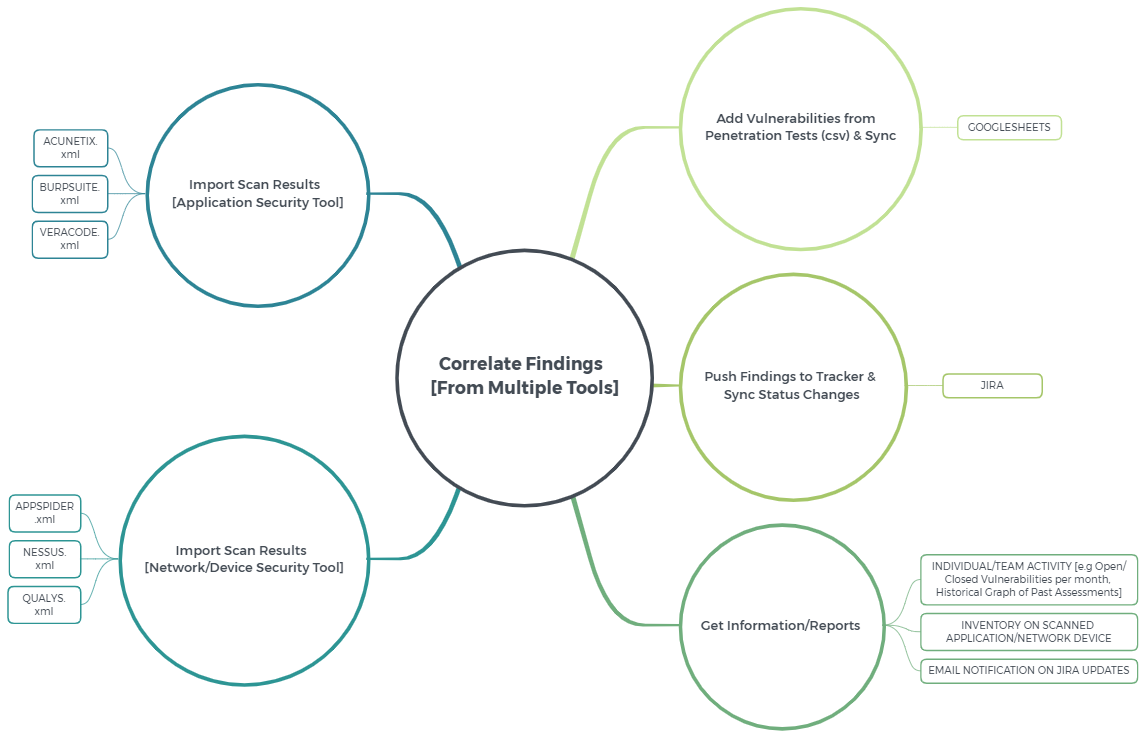
CHALLENGE 2: Correlation and Tracking of Vulnerabilities from Different Sources
Basically, we want to incorporate findings from a variety of security testing data sources into a centralized tool and track them to remediation. Looking at the diagram below from left to right, there are three main tasks needed to solve this:
- Import scan results from security tools / correlate findings.
- Add vulnerabilities from penetration test reports. (It is important that pentesting teams deliver reports in a CSV format, in addition to the typical PDF reports.)
- Push vulnerabilities/findings to the tracker and synchronize changes.

I would advise using DefectDojo to implement this, it can be used in large environments.
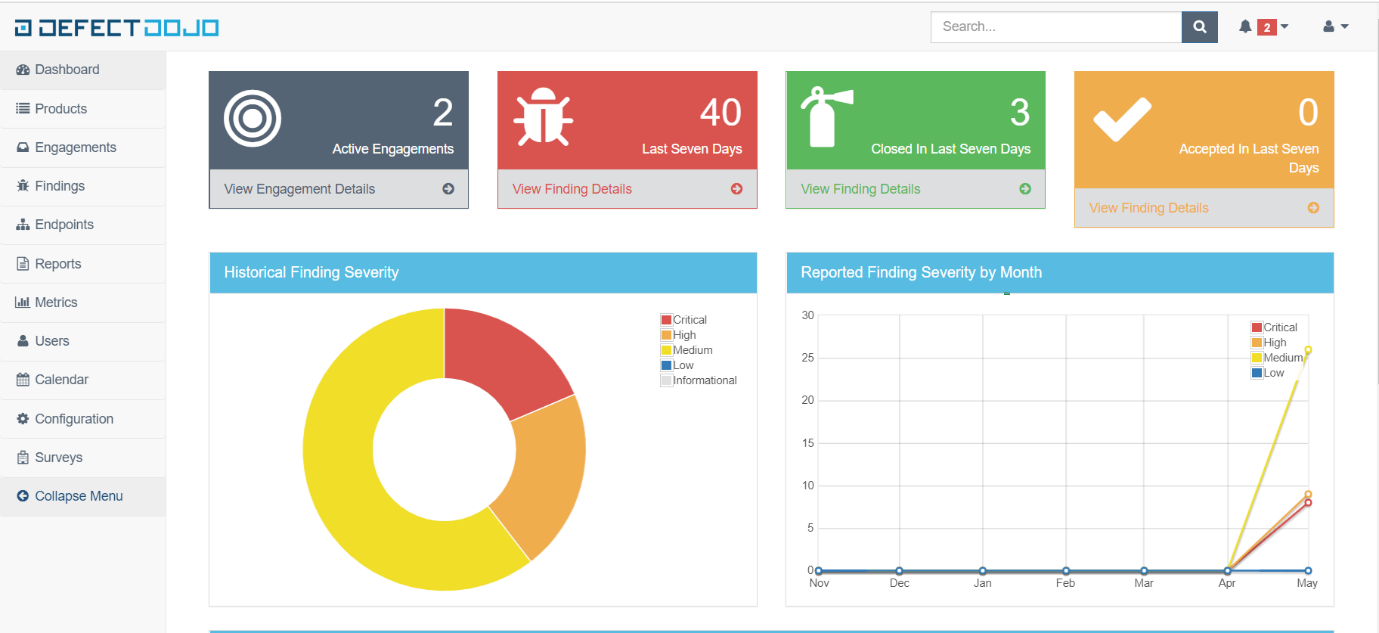
Let us do a high-level walkthrough of the previously mentioned tasks.
[1] Visual Representation of Imported Scan Results (Acunetix & Nessus)
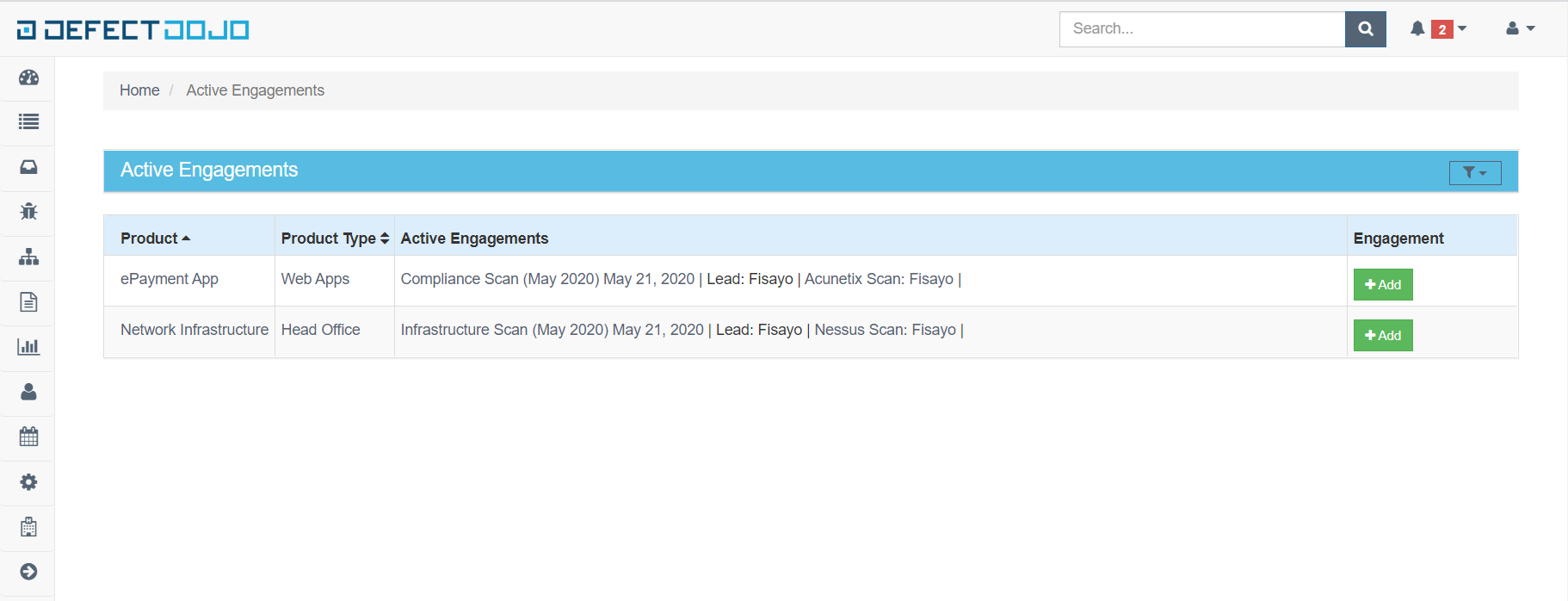
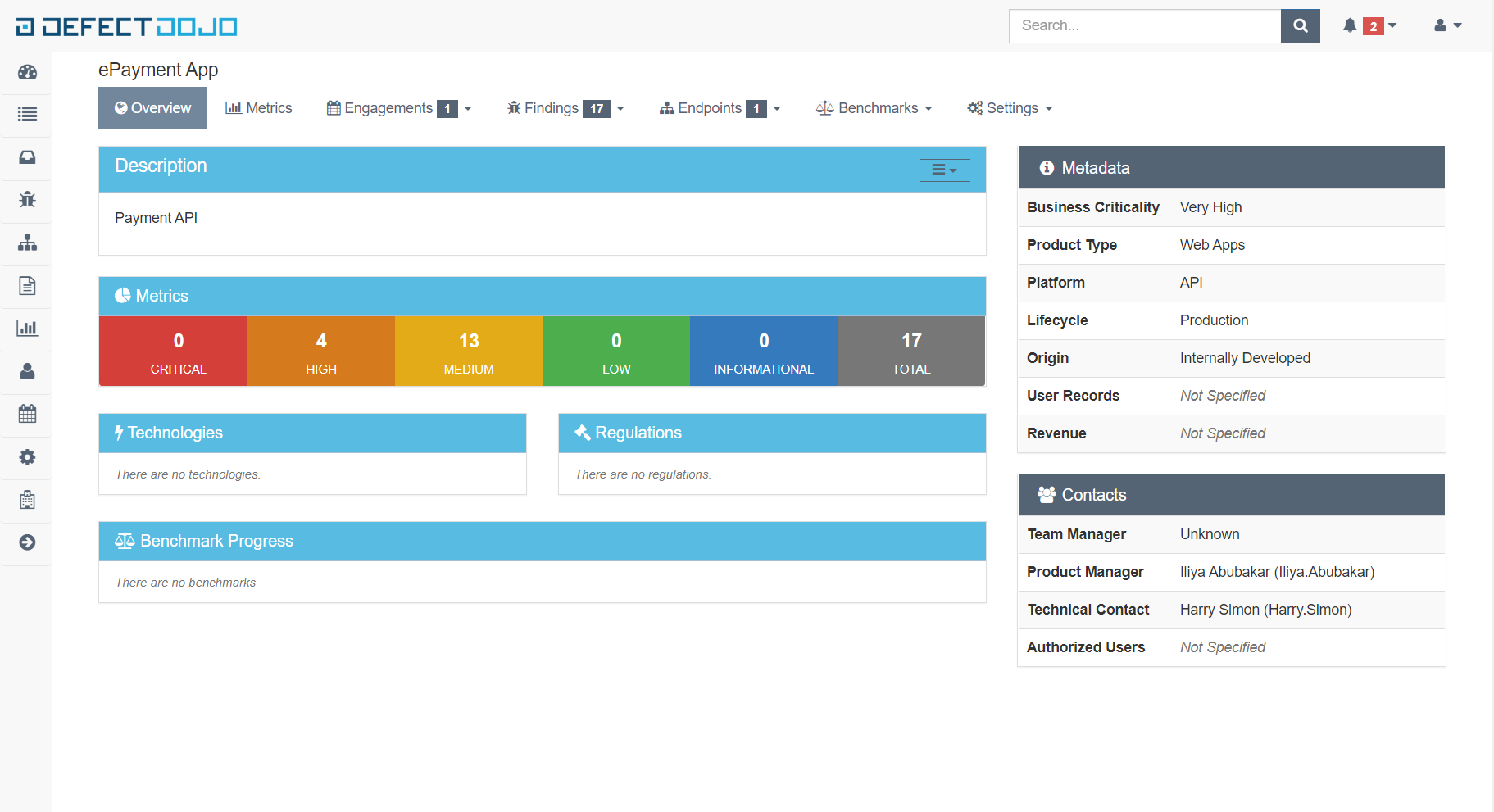
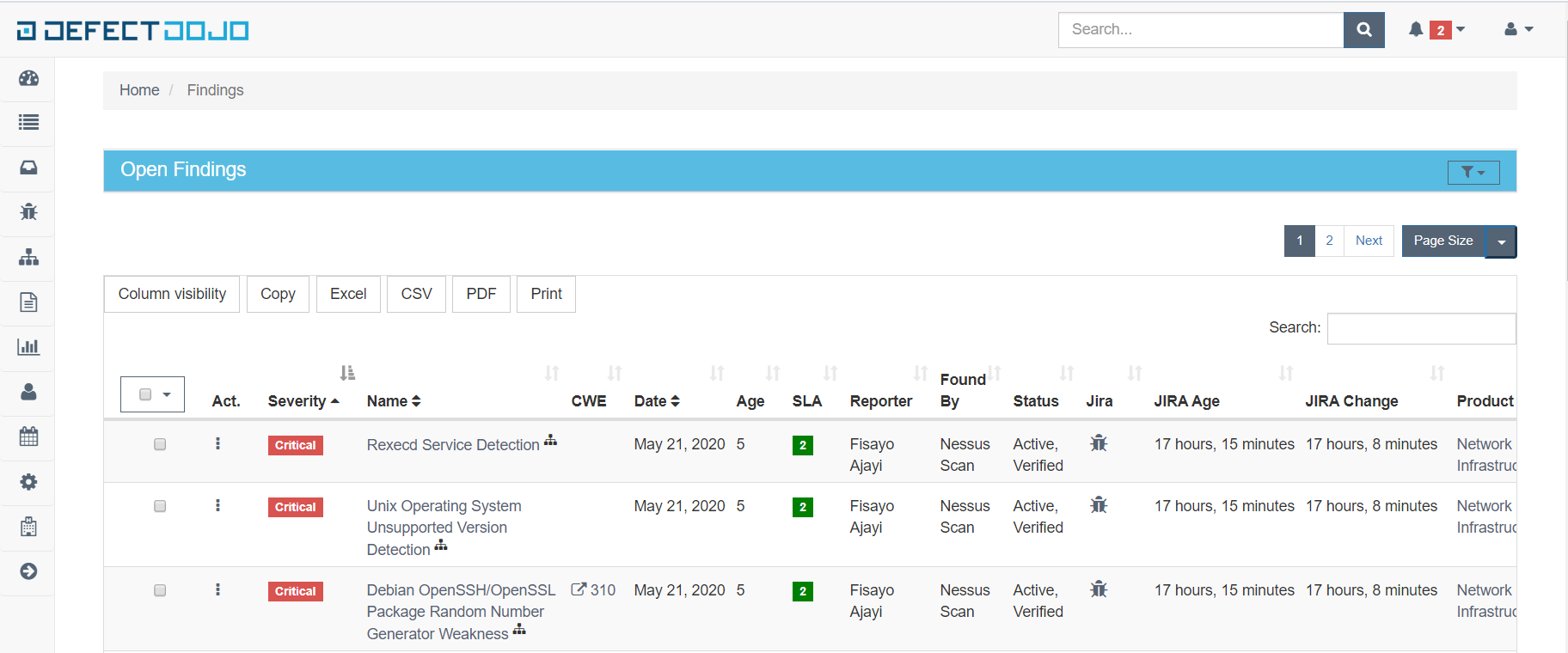
[2] Exported Vulnerabilities to Google Spreadsheet (Sync Additions from PenTest Reports)
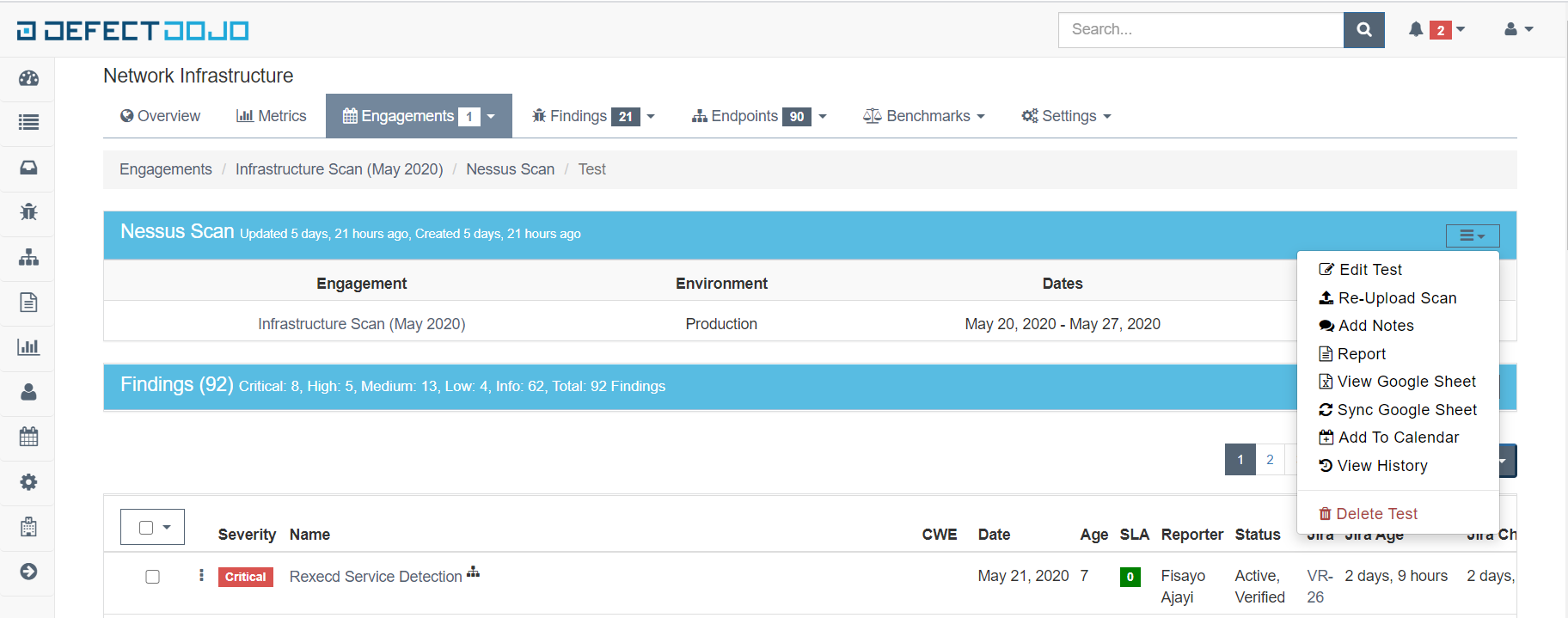
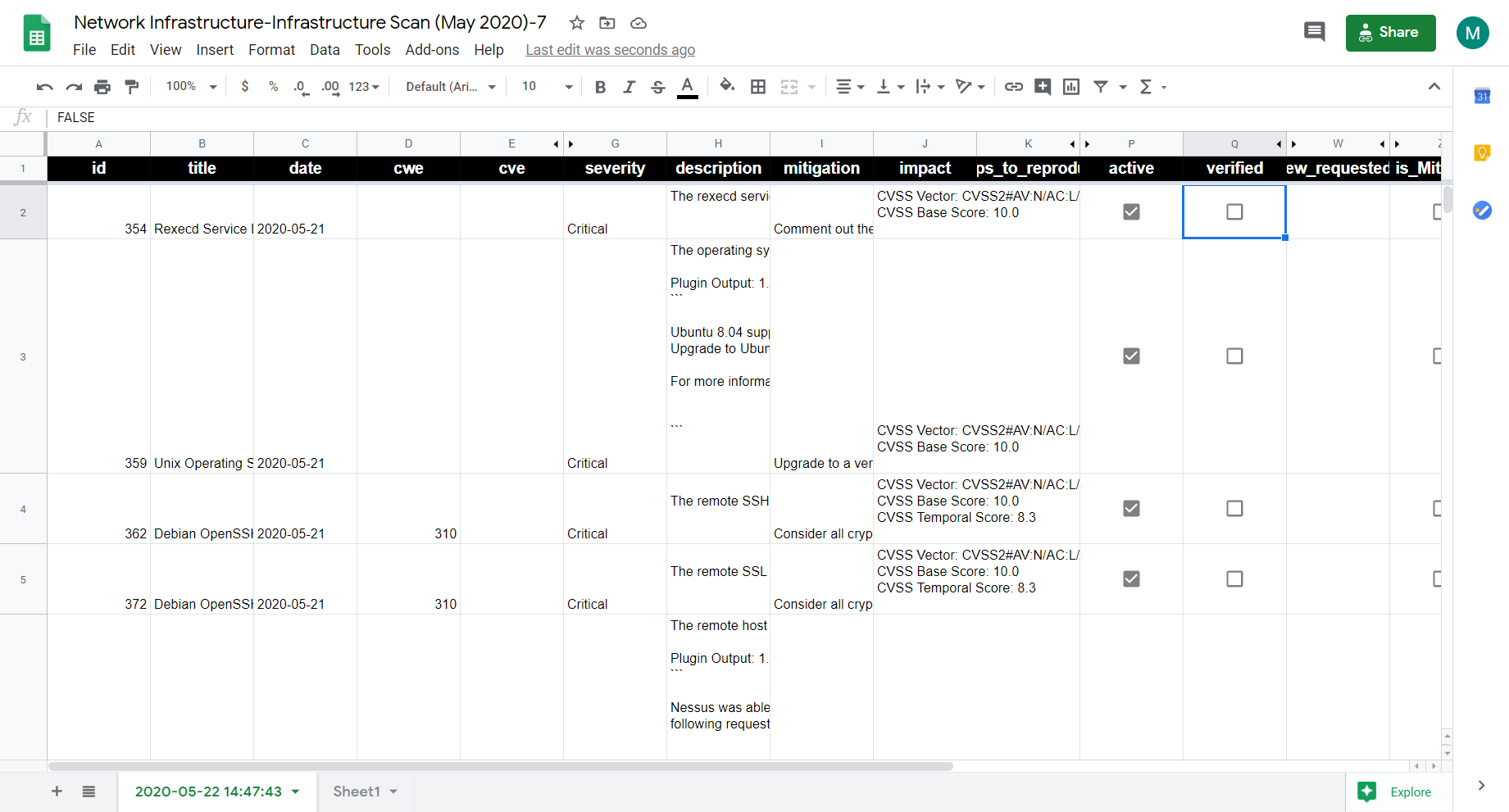
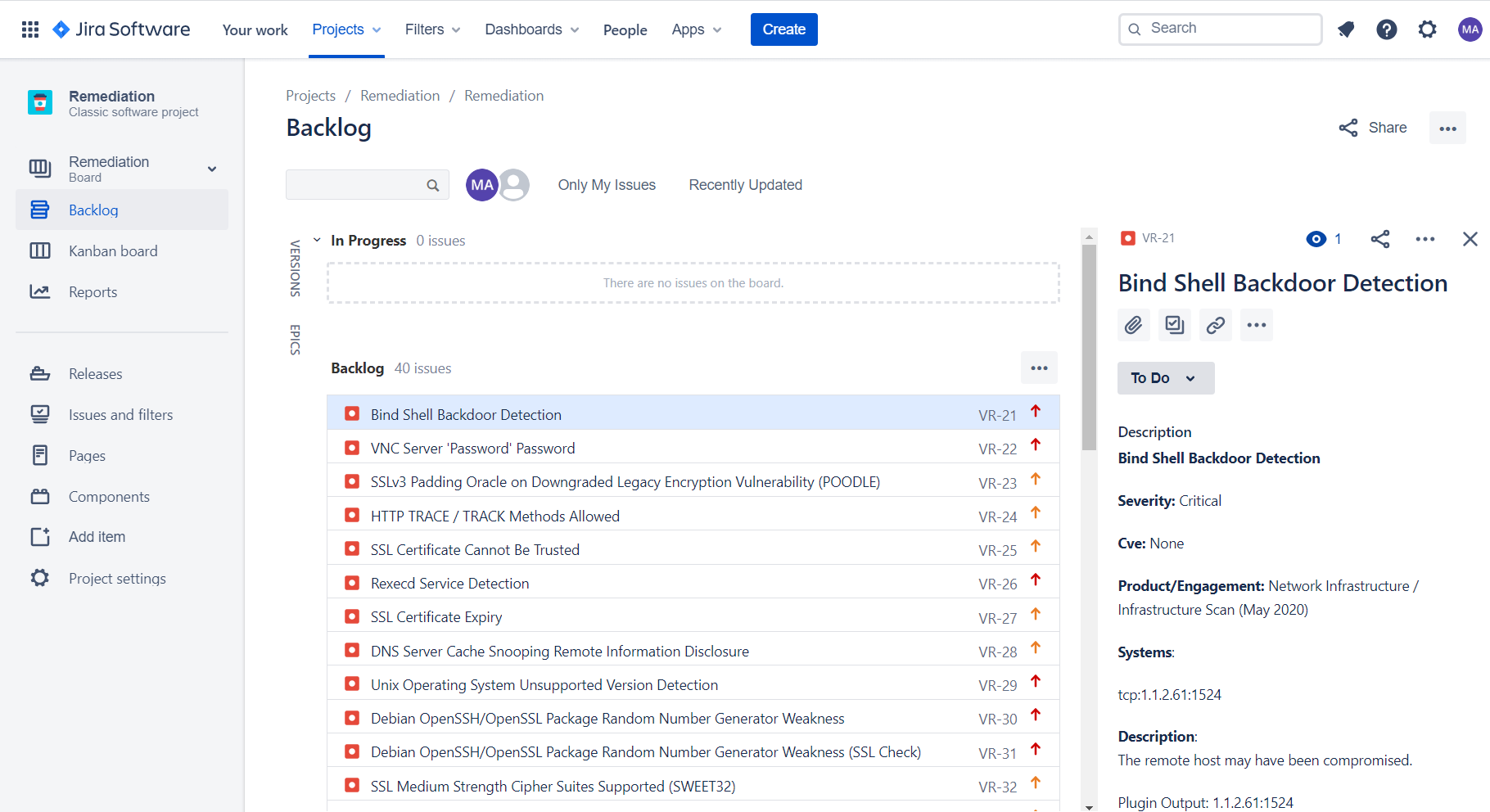
[3.1] Pushed Vulnerabilities to Tracker (Jira)
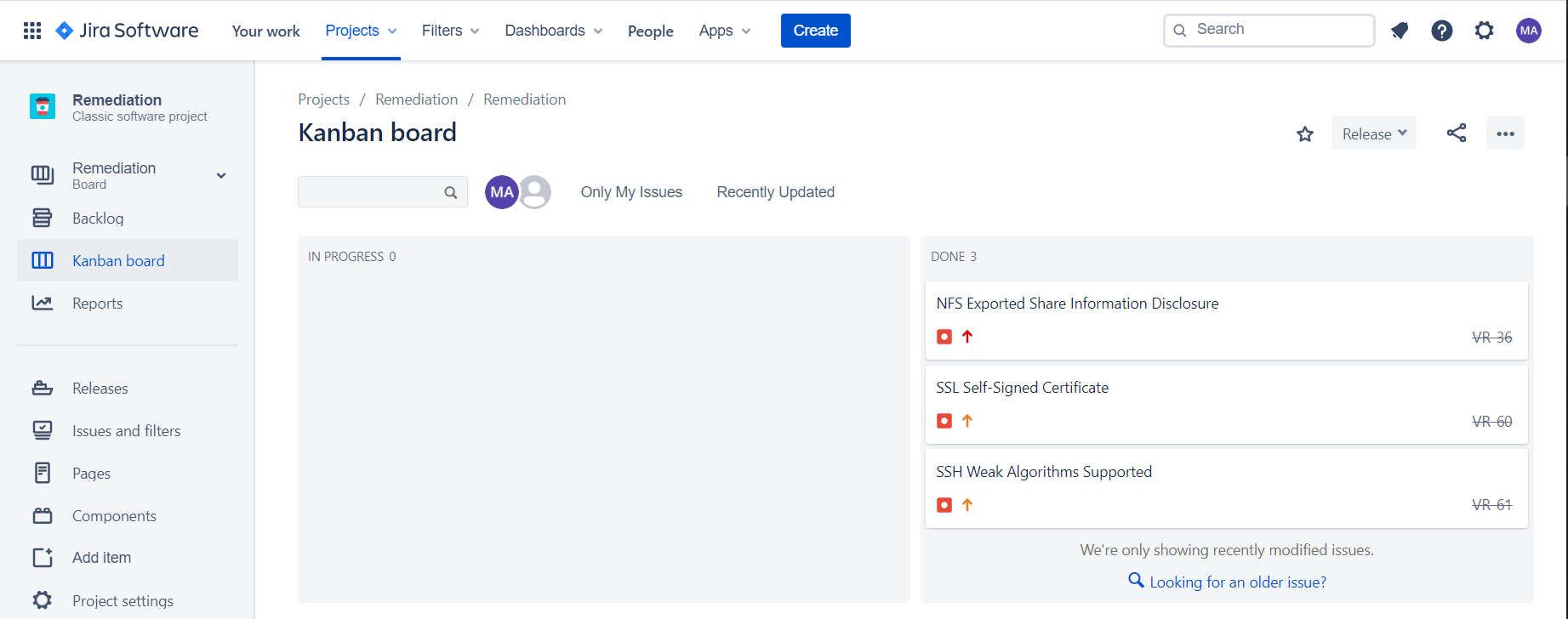
[3.2] Synced Changes (Closed Vulnerabilities)
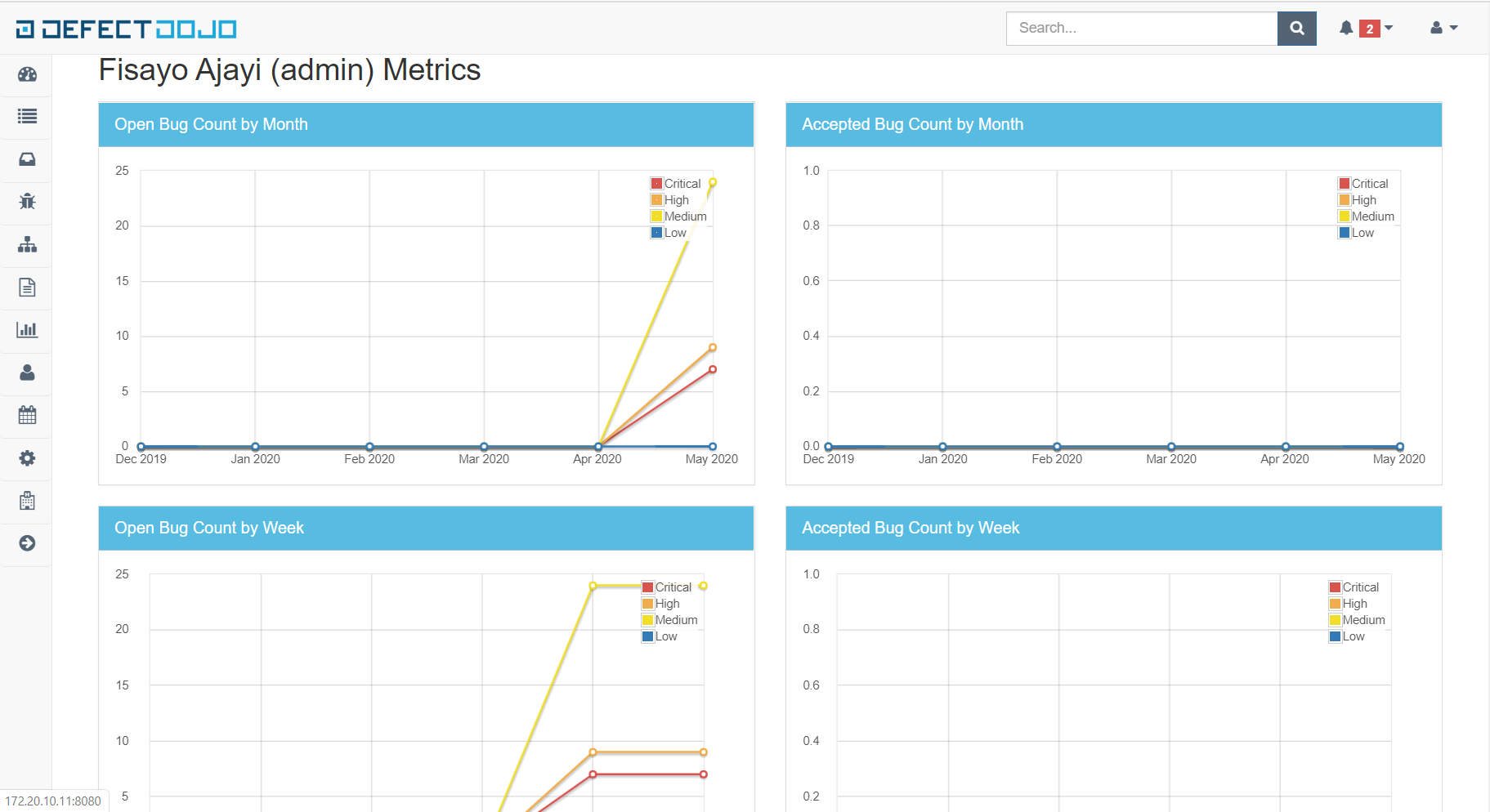
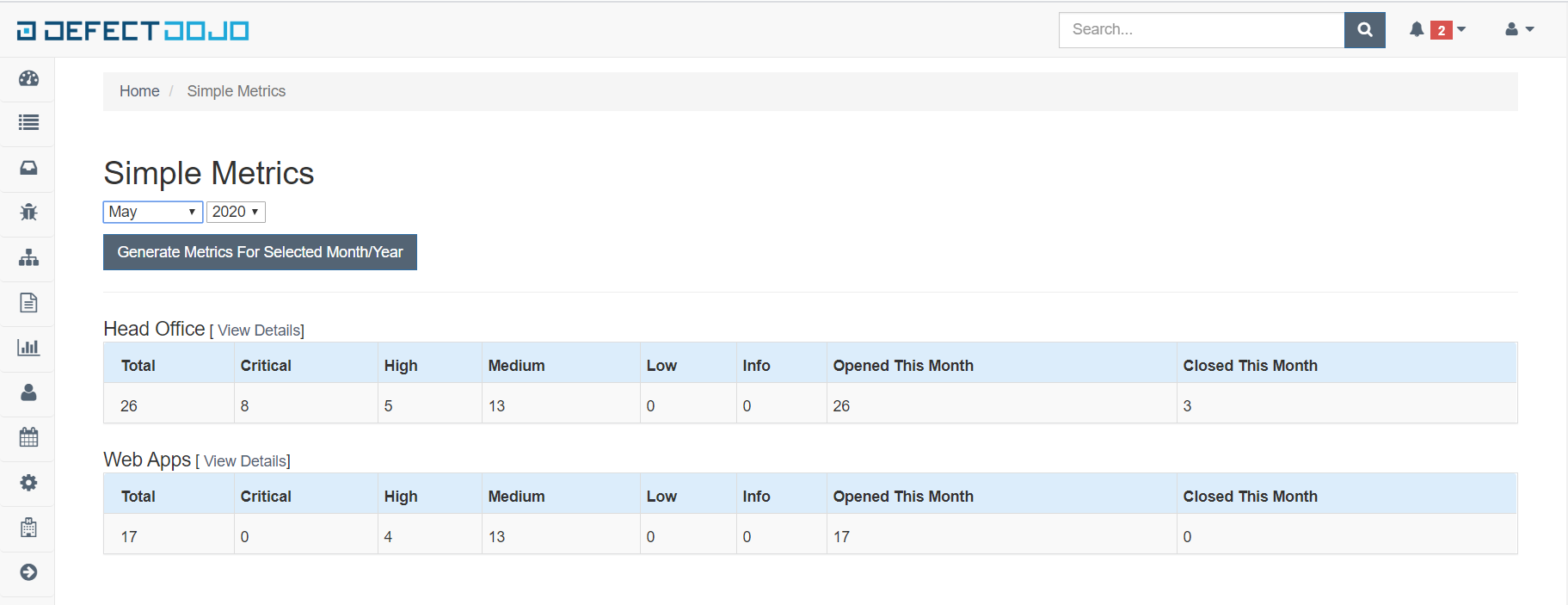
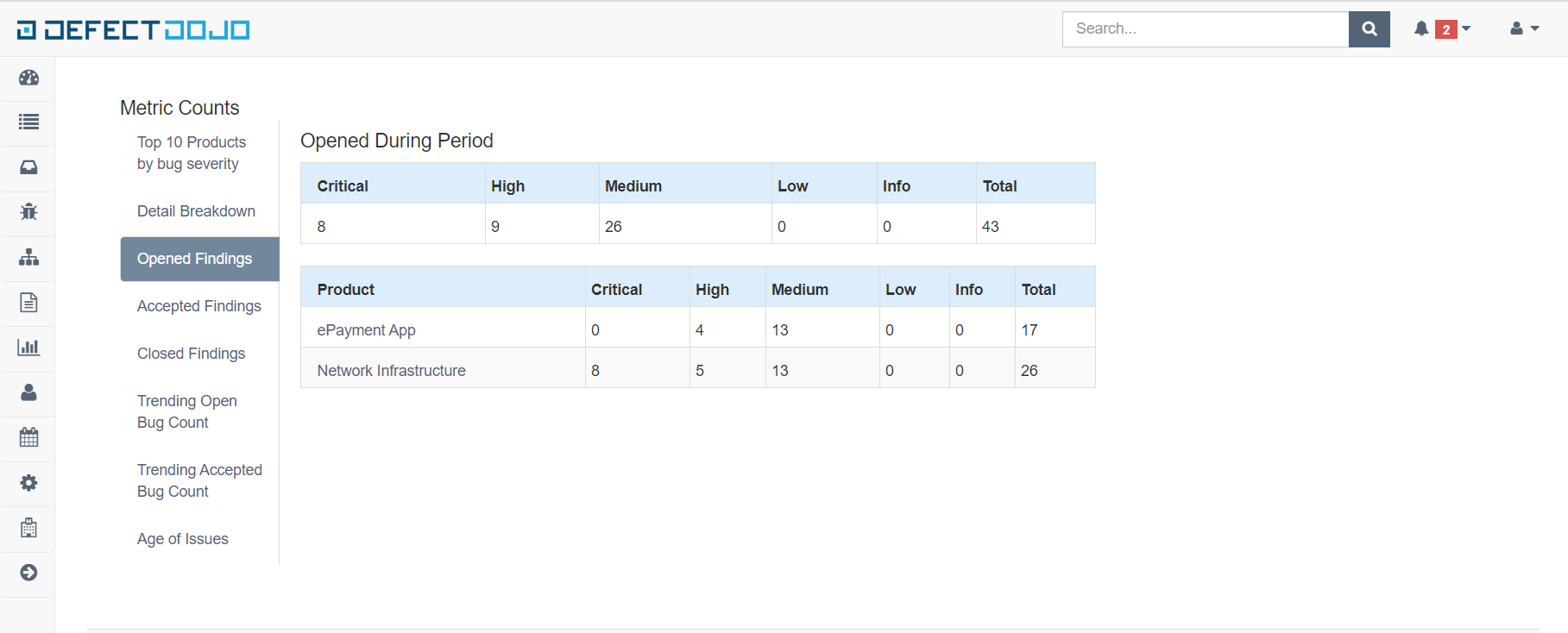
[OTHERS] Metrics, Reports